AWS Systems Manager helps you manage your EC2 instances and On-Premise systems at scale. You can easily get operations insights about the state of your infrastructure. It helps to detect instance issues easily and also it could be patching automation solution to enhance compliance. AWS Systems Manager works for both windows and Linux operating systems and it can be easily integrated with CloudWatch metrics and dashboards. You can also integrate with AWS config.
AWS Systems Manager simplifies setting up services, by automating common or recommended tasks using documents (automation templates). These tasks include, for example, creating required AWS Identity and Access Management (IAM) instance profile roles and setting up operational best practices, such as periodic patch scans and inventory collection.
The following high level AWS Systems Manager diagram shows what it is capable of doing it.
Image source – https://docs.aws.amazon.com/systems-manager
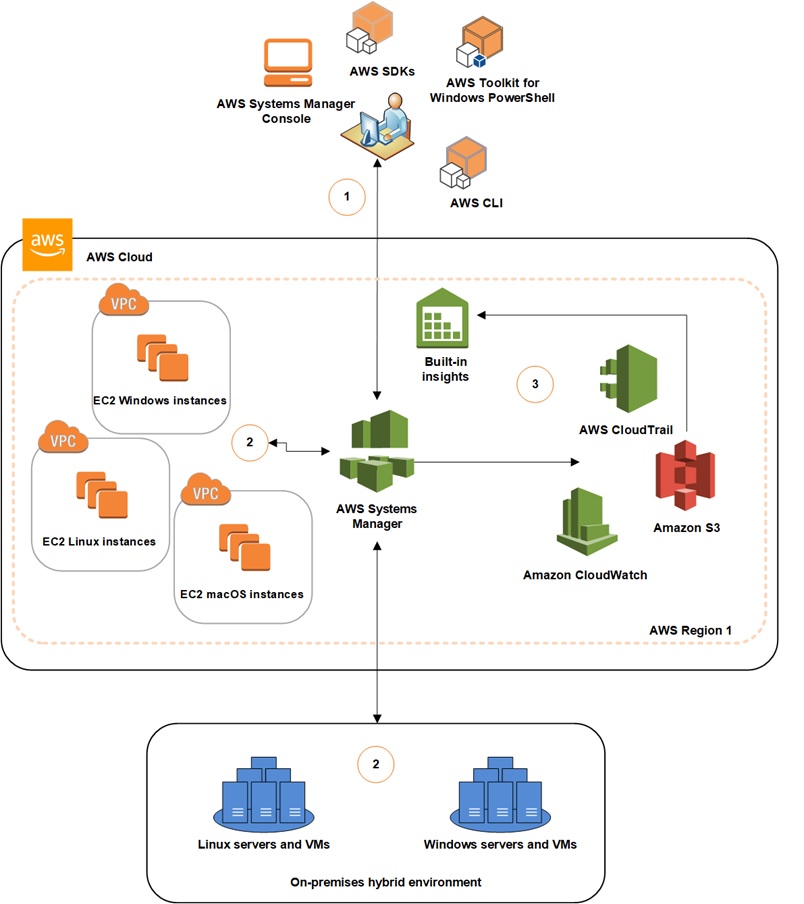
How it Works ?
AWS Systems Manager is agent based solution where you need to install the SSM agent on the EC2, On-premise servers or virtual machines. Systems Manager agents makes it possible for Systems Manager to update, manage, and configure these resources effectively. The agent processes requests from the Systems Manager service in the AWS Cloud, and then runs them as specified in the request. SSM Agent then sends status and execution information back to the Systems Manager service by using the Amazon Message Delivery Service.
SSM agent will be pre-installed on Amazon Linux, Ubuntu and Windows EC2 instances. If you have other Linux variant (Ex: RedHat), you need to install SSM agent manually. The following links will help you to install the agent on the ON-PREM servers.
- Install SSM Agent for a hybrid environment (Windows)
- Install SSM Agent for a hybrid environment (Linux)
AWS System Manager Use-cases
1. Instance/Node Management:
AWS System Manager brings key AWS components together to manage the nodes efficiently and effectively with less human intervention. Compliance management is one of the important feature in SSM. It displays compliance data about Patch Manager patching and State Manager associations. You can also customize the service and create your own compliance types based on your IT or business requirements.
Fleet Manager is a unified user interface (UI) experience that helps you remotely manage your server fleet running on AWS, or on-premises. It helps to view the health and performance status of your entire server fleet from one console. You can also gather data from individual instances to perform common troubleshooting and management tasks from the console.
Inventory, a capability of AWS Systems Manager, automates the process of collecting software inventory from managed instances. You can use Inventory to gather metadata about applications, files, components, patches, and more on your managed instances.
Session Manager helps you to get EC2 instance web based console session and or through the AWS CLI.
Run Common is another key feature of AWS Systems Manager which helps to remotely and securely manage the configuration of your managed instances at scale. Use Run Command to perform on-demand changes such as updating applications or running Linux shell scripts and Windows PowerShell commands on a target set of dozens or hundreds of instances.
State Manager helps you to maintain the instance state for both EC2 and ON-PREM instances. It can also be used to bootstrapped with specific software at startup, joined to a Windows domain (Windows Server instances only), or patched with specific software updates.
Patch Manager is ultimate feature of systems manager which automates the process of patching your managed instances with both security related and other types of updates. You can use Patch Manager to apply patches for both operating systems and applications. This capability allows you to scan instances for missing patches and apply missing patches individually or to large groups of instances by using EC2 instance tags. Patch Manager uses patch baselines, which can include rules for auto-approving patches within days of their release, and a list of approved and rejected patches.
2. Operations Management
Incident Management – Resolve application issues faster with automated incident response plans. Incident Manager helps by engaging responders, tracking incident updates, automating runbook steps, enabling chat-based collaboration, and streamlining post-incident analysis.
PHD – Personal Health Dashboard – It helps to display the overall environment health. It also provides the classification by region, time and event category.
Ops Center – Consolidate your operations items (OpsItems) into a single location that provides contextual information, historical guidance, and quick solution steps.
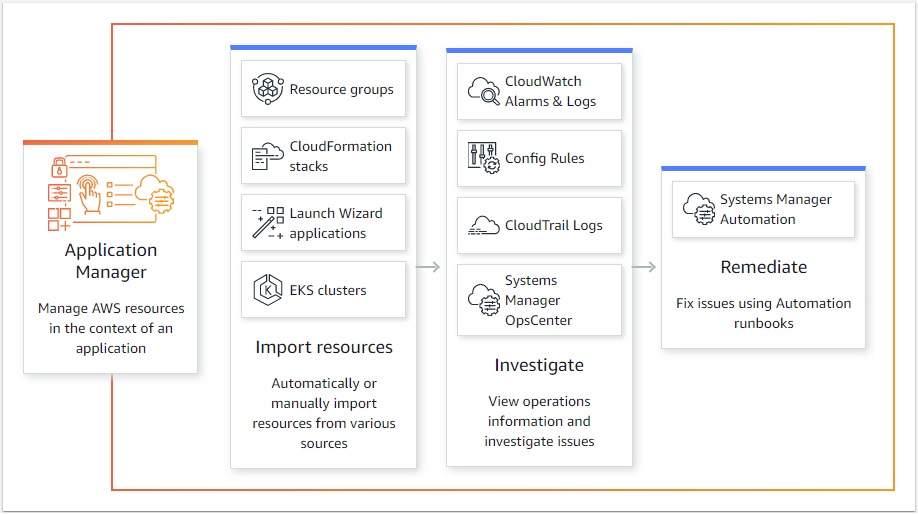
3. Application Management
Investigate and remediate issues with AWS resources in the context of an application from one console. Application Manager automatically imports and displays resources that are based on AWS CloudFormation stacks, AWS Resource Groups, Amazon EKS clusters, and Launch Wizard deployments. The system displays these resources in predefined application categories. Application Manager integrates with Amazon CloudWatch to provide real-time operational metrics and alarms. You can choose individual resources in your application tree to view alarms at each component level.
4. Change management
AWS System Manager Change management module simplify how your team requests, approves, implements, and reports on operational changes. Manage changes to your application configuration and infrastructure, both in AWS and on premises. It provides more than the typical support for helping track and audit changes to your applications and infrastructure. Change Manager reports on why changes were requested across your organization, who approved them, and how they were implemented. Change Manager is integrated with AWS Organizations. You can make changes across multiple AWS accounts, and easily view multi-account reporting details, from a single delegated administrator account.
5. Document – Shared Resources
AWS System Manager – Documents provides the readymade automation templates to perform most of the AWS platform level operational tasks automation using JSON/YAML. These resources can be quickly cloned and modified as per your requirement. These documents also can be scheduled perform certain tasks or monitor various stuff on the node/instance.
AWS SSM Document Type:
Command document: Run Command uses command documents to run commands. State Manager uses command documents to apply a configuration. Maintenance Windows uses command documents to apply a configuration based on the specified schedule.
Automation document: Automation uses automation documents to perform common maintenance and deployment tasks such as creating or updating an AMI. State Manager uses automation documents to apply a configuration. Maintenance Windows uses automation documents to perform common maintenance and deployment tasks based on the specified schedule.
Package document: SSM Distributor uses a package document that includes attached ZIP archive files that contain software or assets to install on managed instances.
Session document: Session Manager uses session documents to determine which type of session to start, such as a port forwarding session, a session to run an interactive command, or a session to create an SSH tunnel.
Policy document: Systems Manager Inventory uses the policy document with a State Manager association to collect inventory data from managed instances.
Change Calendar document: Systems Manager Change Calendar uses the Change Calendar document type to allow or prevent Automation actions from changing your environment.
Hope this article have given quick overview about AWS system Manager. Keep
Leave a Reply