ChatGPT made a big revolution in the 21st century and called big giants to think differently rather than polishing existing products. ChatGPT can respond like an actual human or even better. ChatBots become quite popular to provide basic information for simple queries. ChatGPT is powered by AI(Artificial intelligence) with deep learning techniques and developed by […]
DevOps
How to get root access on the docker host filesystem?
How to gain root access to the host filesystem in a Docker environment when you don’t have root or “sudo” privileges on the host? Since many Kubernetes systems still run on Docker and a transition to Podman is ongoing, this article provides a solution to allow access to the host filesystem with root privileges from […]
How to login to Docker Container/Pods ? Kubernetes/OpenShift
Container is a lightweight, standalone, and executable package of software that includes everything needed to run a piece of software, including the code, a runtime, system tools, libraries, and settings. containers are built from images, which are essentially snapshots of a container at a specific point in time. Docker is most widely used container solution […]
Kubernetes (k8s)- Disaster Recovery Strategies
A disaster recovery (DR) strategy is a plan for maintaining and recovering critical systems and data in the event of a disaster or other interruption. Kubernetes (also known as K8s) is a popular open-source container orchestration system that allows users to automate containerized applications’ deployment, scaling, and management. A disaster recovery (DR) test is important […]
Cloud Instance Backup / VM Backup strategies
Backing up your cloud instances is important for various reasons. Cloud instances can experience data loss due to a variety of reasons, including hardware failure, software bugs, and cyber attacks. Backing up your instances can help protect against data loss by providing a copy of your data that you can use to restore your instance […]
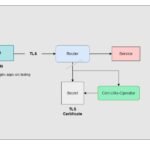
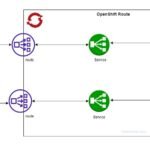
Openshift secure route TLS – Is it possible to use secrets?
The OpenShift Container Platform provides multiple options to provide access to external clients. The route is one of the methods to provide the access to external clients. We can enable TLS termination on route to encrpt the data sent over to the external clients. We need to update the valid certificate and private key in […]
How to expose service on the Openshift? Enable TLS secure route?
Openshift provides multiple options to expose the application to external traffic. When you deploy a pod in openshift, kubernetes allocates the internal IP address for each pod. If you are deploying an nginx container to serve the webpage, the nginx pod will have a unique internal IP address but it can’t be accessed outside the […]
Quick vi editor hacks for DevOps Engineers
DevOps engineers have to work on a wide range of toolsets to meet the organization’s requirements. In the DevOps role, one tool is going to stay forever to make an engineer’s life simple and more powerful. As the article heading says, it is “vi” editor. The “vi” editor is created by Bill Joy in 1976 […]
kubernetes – Traefik Middlewares – Part 5
Middleware helps to tweak the requests before reaching the actual service in kubernetes. Traefik support multiple middleware and one can use them depending on their needs. Some of the middleware helps with basic authentication, and some of the middleware helps with redirection. Middleware also helps to modify the request headers for incoming requests. The following […]
kubernetes traefik – Managing TLS Certificates – Part 4
How to configure HTTPS for your applications on the Kubernetes cluster? How to manage TLS certificates using traefik? Traefik proxy is a very popular ingress controller in kubernetes environments. It supports both HTTPS (router) and TLS connections. This article explains how to configure TLS connection and obtain TLS certificates dynamically using pebble (Only for the […]