All new Macbooks are shipping with M1 / M2 chips which are based on ARM (Advanced RISC Machines). Apple is no longer releasing the x86-based MacBooks to eliminate the intel dependencies for any advancement. It also brings a lot of challenges for people who are very familiar with intel macbooks which support most of the […]
Virtualization
Virtualization & Hypervisor – Basic Interview Questions
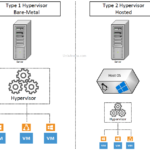
Virtualization helps to decouple the Operating systems and applications from the hardware layer. Virtualization is the process of creating a virtual or software-based representation like a virtual server, application, network, storage resources. Hypervisor is one of the most popular virtualizations technology for servers and operating systems. This enables the IT organization to run more than […]
Meltdown and Spectre Vulnerabilities – Big Threats
Meltdown and Spectre Vulnerabilities have made 80% of servers as Vulnerable in overnight, thanks to Google Project Zero team and other security researchers who have brought such a worst vulnerabilities to the world (At least now). Meltdown vulnerability basically melts security boundaries which are normally enforced by the hardware (CPU). Spectre name is based on the root cause, “speculative […]
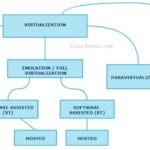
Para virtualization vs Full virtualization vs Hardware assisted Virtualization
Virtualization is nothing but abstracting operating system, application, storage or network away from the true underlying hardware or software. It creates the illusion of physical hardware to achieve the goal of operating system isolation. In last decade, data centers were occupied by a large number of physical servers, network switches, storage devices. It consumed a lot of […]
Do not virtualize your Environment using Hypervisor !
Virtualization is definitely saving the IT cost and most of the companies are benefiting from it.But at the same time, you should not virtualize the all the environment using hypervisors without analyzing it. Hypervisor Virtualization may not be a good choice for heavy work load systems and some specific applications. These items needs to be identified prior […]