How do you renew the kubernetes expired certificate? Kubernetes uses various certificates for secure communication within the cluster. These certificates are essential for securing communication between various components, such as API servers, kubelets, and etcd. Environment: root@kmaster1:~# kubectl version –shortClient Version: v1.22.0Server Version: v1.22.15root@kmaster1:~# Here are some of the important certificates used in Kubernetes: How […]
kubernetes
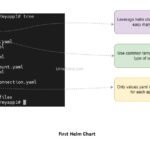
How do you create a first helm chart? Kubernetes Package Manager
Helm is a package manager for Kubernetes that allows you to define, install, and upgrade even the most complex Kubernetes applications. Helm is one of the most vital tools in DevOps. Kustomize is a built-in tool for Kubernetes that allows you to customize raw, template-free YAML files for multiple purposes, including managing multiple versions of […]
kubectl – Let’s colourize the output
kubectl is a command-line tool for interacting with Kubernetes clusters. It is the primary interface for managing and controlling Kubernetes clusters, including deploying applications, inspecting cluster resources, scaling workloads, debugging, and performing various administrative tasks. kubecolor is an alternative command-line tool to interact with kubernetes clusters and provide the colorized output, unlike the kubectl command. […]
How to secure Kubernetes cluster ? Why etcd backup is important ?
Securing etcd in a Kubernetes cluster is crucial as etcd is a distributed key-value store that holds the cluster’s configuration data, including sensitive information. It acts as a reliable and highly available database that stores information about the cluster’s configuration, its current state, and metadata. What “etcd” does in kubernetes ? 1. Configuration Data Store: […]
Kubernetes: How Blue-Green Deployment works?
Blue-green deployment involves simultaneously operating two application environments within a production cluster. In this deployment approach, the stable version of the application is deployed in the first environment (blue), while the new version is deployed in the second environment (green). By default, Kubernetes performs a rolling update of a deployment. As part of the rollout […]
How to get root access on the docker host filesystem?
How to gain root access to the host filesystem in a Docker environment when you don’t have root or “sudo” privileges on the host? Since many Kubernetes systems still run on Docker and a transition to Podman is ongoing, this article provides a solution to allow access to the host filesystem with root privileges from […]
Kubernetes – How to cleanup the failed pods from all namespaces ?
In the Kubernetes environment, we could often see that pods might fail due to various reasons. Most of the time, it could be related to config issues or capacity-related issues. In such conditions, you could see the pod status could be “pending”, “Crashloopbackoff”, “evicted”, “Failed”, “ContainerCannotRun”, “Error”, “ContainerCreating” etc. As a DevOps engineer, you need […]
How to login to Docker Container/Pods ? Kubernetes/OpenShift
Container is a lightweight, standalone, and executable package of software that includes everything needed to run a piece of software, including the code, a runtime, system tools, libraries, and settings. containers are built from images, which are essentially snapshots of a container at a specific point in time. Docker is most widely used container solution […]
Kubernetes (k8s)- Disaster Recovery Strategies
A disaster recovery (DR) strategy is a plan for maintaining and recovering critical systems and data in the event of a disaster or other interruption. Kubernetes (also known as K8s) is a popular open-source container orchestration system that allows users to automate containerized applications’ deployment, scaling, and management. A disaster recovery (DR) test is important […]
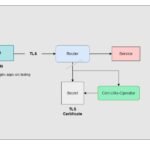
Openshift secure route TLS – Is it possible to use secrets?
The OpenShift Container Platform provides multiple options to provide access to external clients. The route is one of the methods to provide the access to external clients. We can enable TLS termination on route to encrpt the data sent over to the external clients. We need to update the valid certificate and private key in […]